
Welcome to the team, kid. I have something for you to get your feet wet. Our client has a newly hired employee who saw a suspicious-looking janitor exiting his office as he was about to return from lunch.
I want you to investigate if there was user activity while the user was away between 12:05 PM to 12:45 PM on the 19th of November 2022. If there are, figure out what files were accessed and exfiltrated externally.
You'll be accessing a live system, but use the disk image already exported to the C:\Users\THM-RFedora\Desktop\kape-results\C directory for your investigation. The link to the tools that you'll need is in C:\Users\THM-RFedora\Desktop\tools
Finally, I want to remind you that you signed an NDA, so avoid viewing any files classified as top secret. I don't want us to get into trouble.
Initial investigations reveal that someone accessed the user's computer during the previously specified timeframe.
Whoever this someone is, it is evident they already know what to search for. Hmm. Curious.
What file type was searched for using the search bar in Windows Explorer?
After we deployed the machine, we have tools on the C:\Tools folder and evidence on the Kape result folder on the desktop.
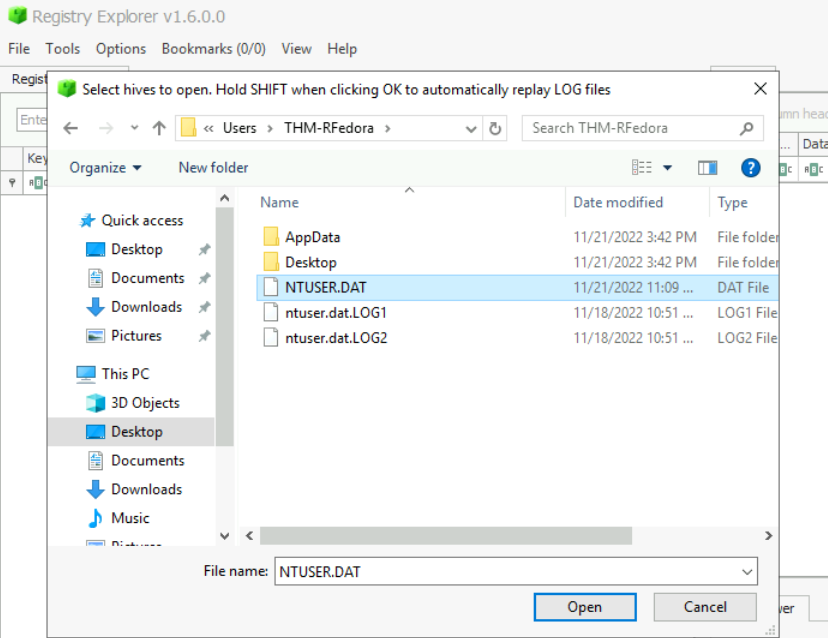
Speaking about Windows Search, we can inspect WordWheelQuery registry key from the only non-default user on this system with Registry Explorer tool.
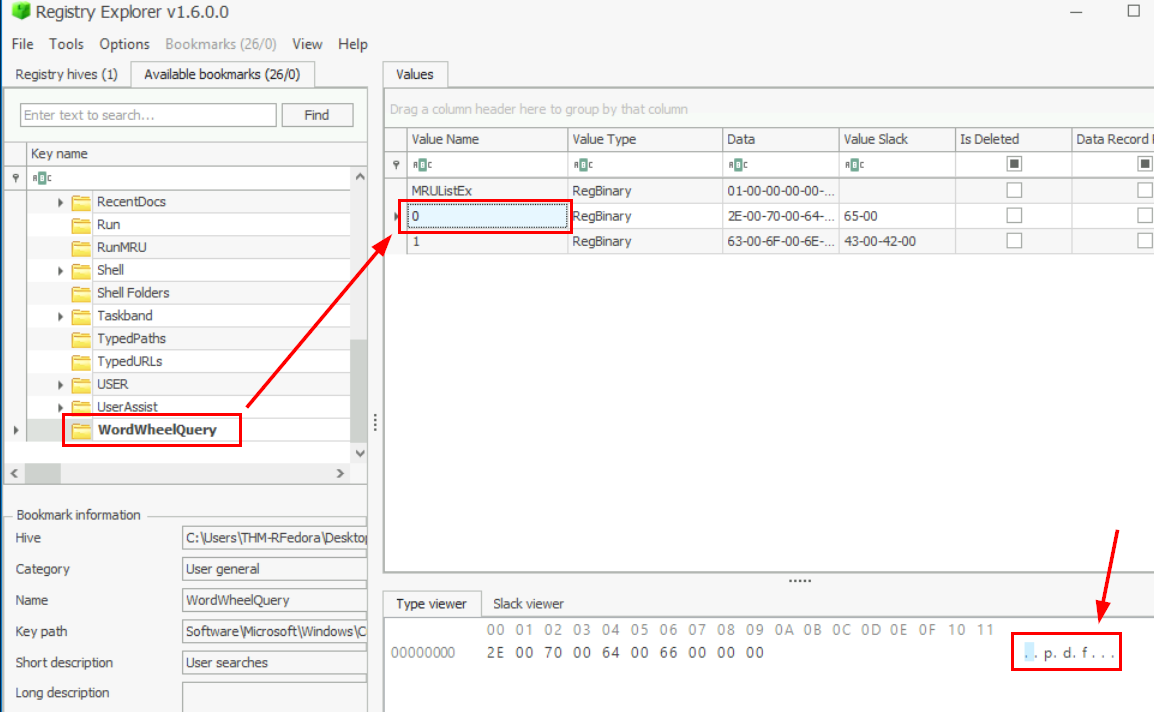
Registry Explorer 1.6 is quite an old version but could still get a job done, we could see that on the first record from WordWheelQuery registry is ".pdf" which is the first keyword searched and the answer of this question.
.pdf
What top-secret keyword was searched for using the search bar in Windows Explorer?
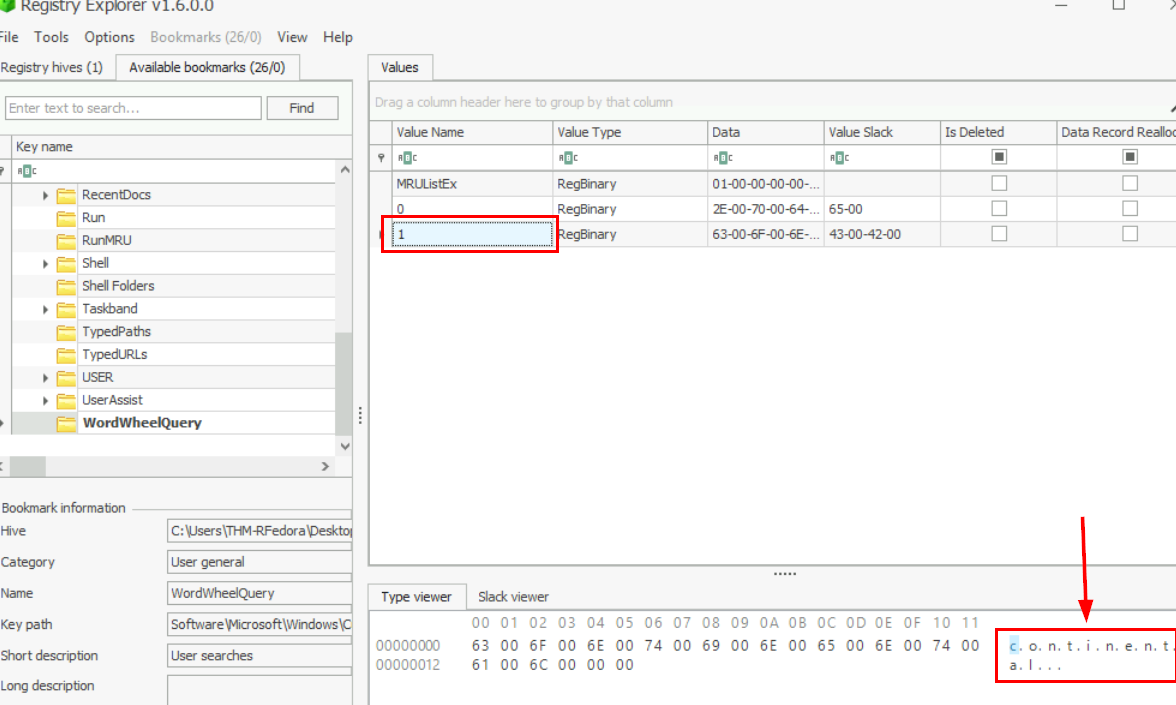
Inspecting the second record, reveal the second keyword that was searched with Windows Search.
continental
Not surprisingly, they quickly found what they are looking for in a matter of minutes.
Ha! They seem to have hit a snag! They needed something first before they could continue.
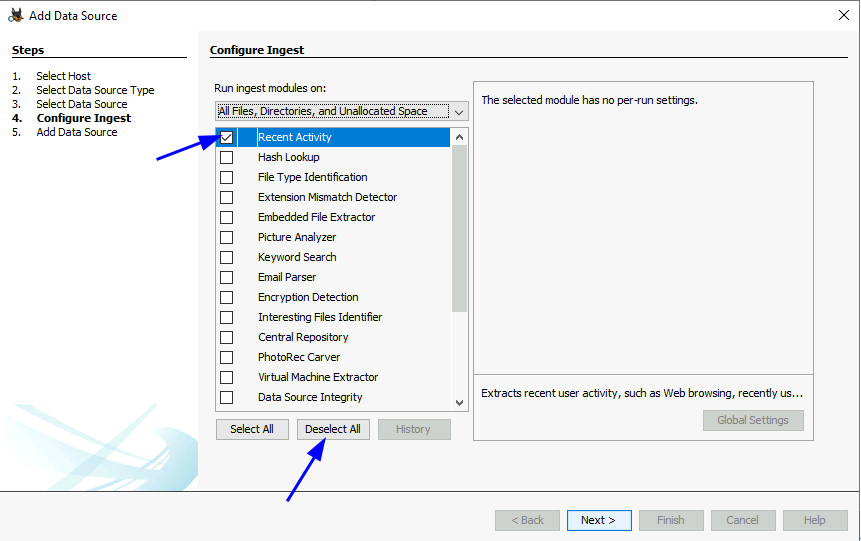
Note: When using the Autopsy Tool, you can speed up the load times by only selecting "Recent Activity" when configuring the Ingest settings.
What is the name of the downloaded file to the Downloads folder?
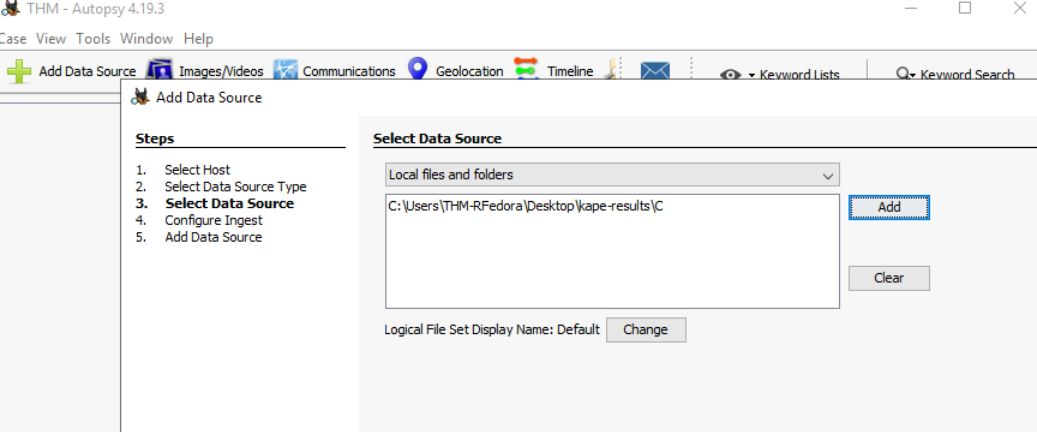
We have to use Autopsy for this one so after create a new case, we have to specify the folder as our logical files like this then follow the guide provides to only select Recent Activity injest module to run.
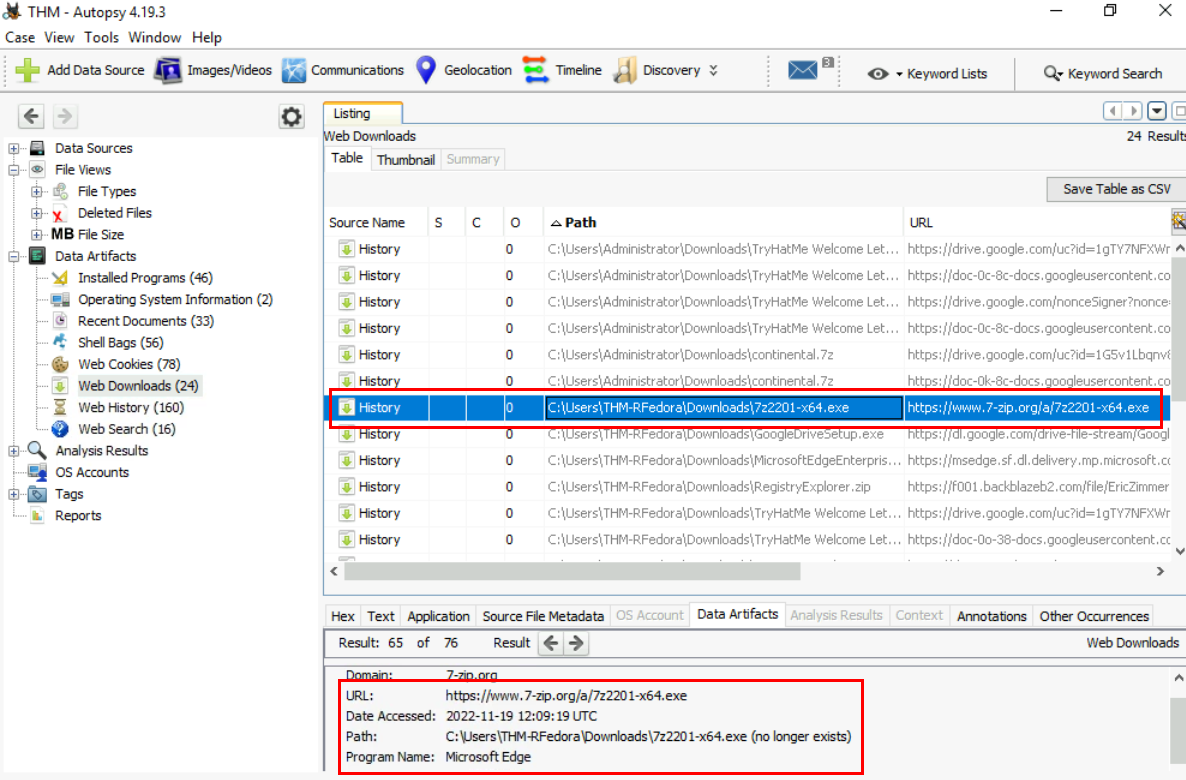
Wait a while for the result which then we can look into "Web Downloads" to find which files were downloaded to user's download folder and we could see that user downloaded continental.7z which then downloaded the installer of 7zip, which mean the 7z is not installed on the system and user downloaded it to extract the file.
7z2201-x64.exe
When was the file from the previous question downloaded? (YYYY-MM-DD HH:MM:SS UTC)
2022-11-19 12:09:19 UTC
Thanks to the previously downloaded file, a PNG file was opened. When was this file opened? (YYYY-MM-DD HH:MM:SS)
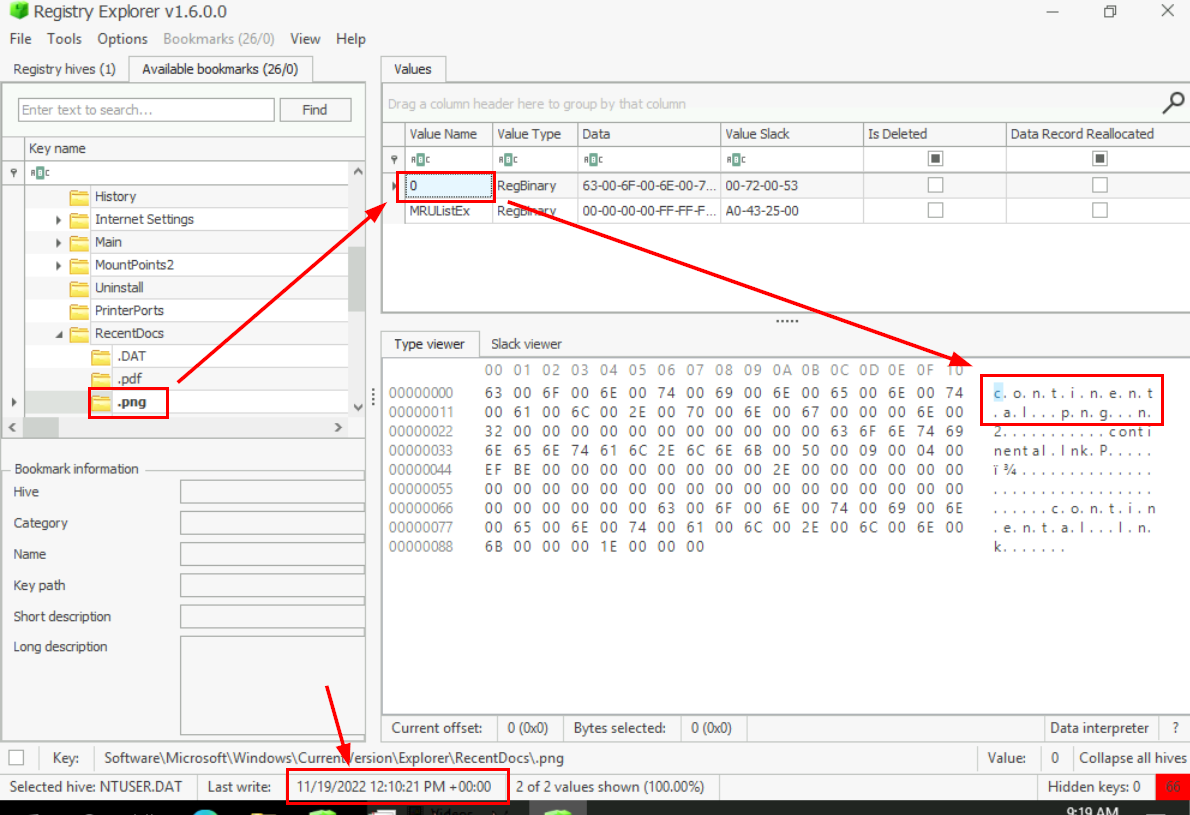
We have to go back to the Registry Explorer and inspect RecentDocs registry key which separate each file extenstion to each subkey so we can inspect .png sub key to find the only file that was opened by the user and the Last write timestamp of this registry is the timestamp that the file was opened.
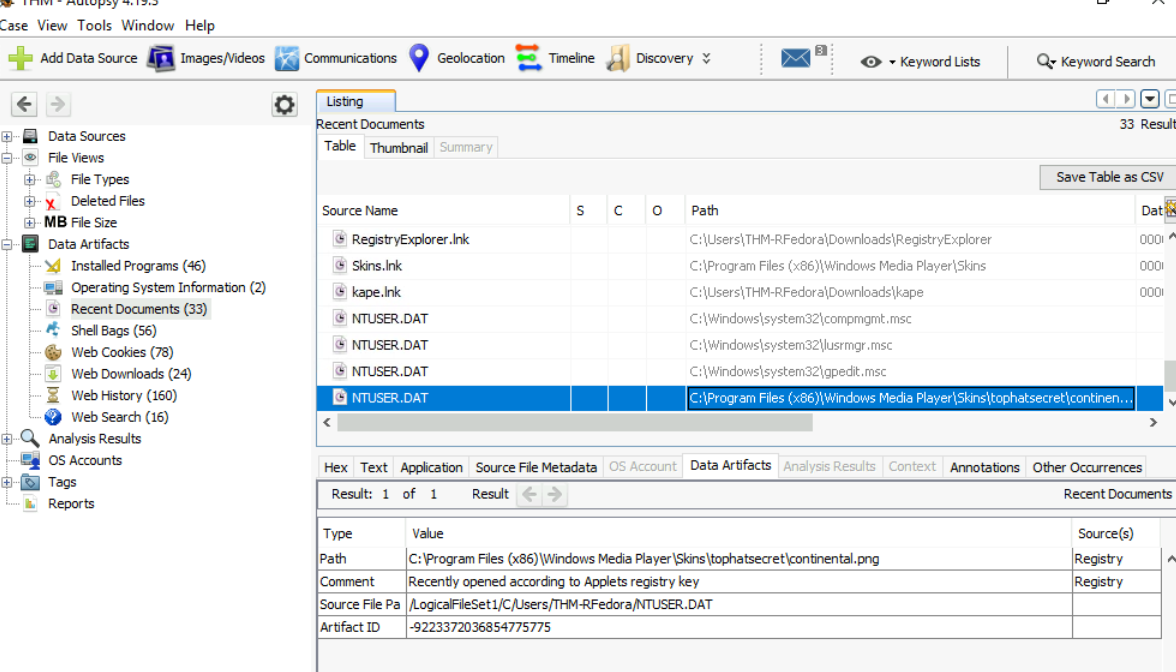
We could even find the full path of this file on Autopsy like this.
2022-11-19 12:10:21
Uh oh. They've hit the jackpot and are now preparing to exfiltrate data outside the network.
There is no way to do it via USB. So what's their other option?
A text file was created in the Desktop folder. How many times was this file opened?
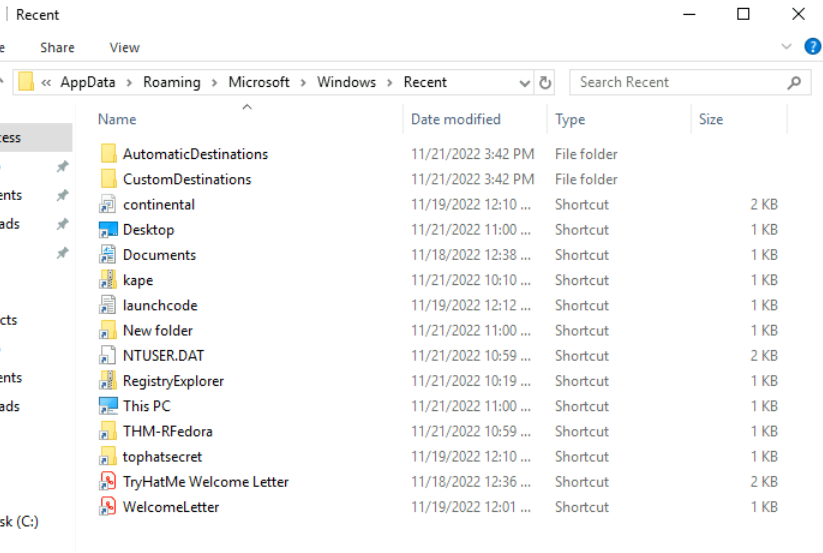
We also have JumpLists as our evidence and from the shortcut file inside this folder, we can see that launchcode is likely to be that text file so we have to parse JumpLists to find out how many times this file was opened.
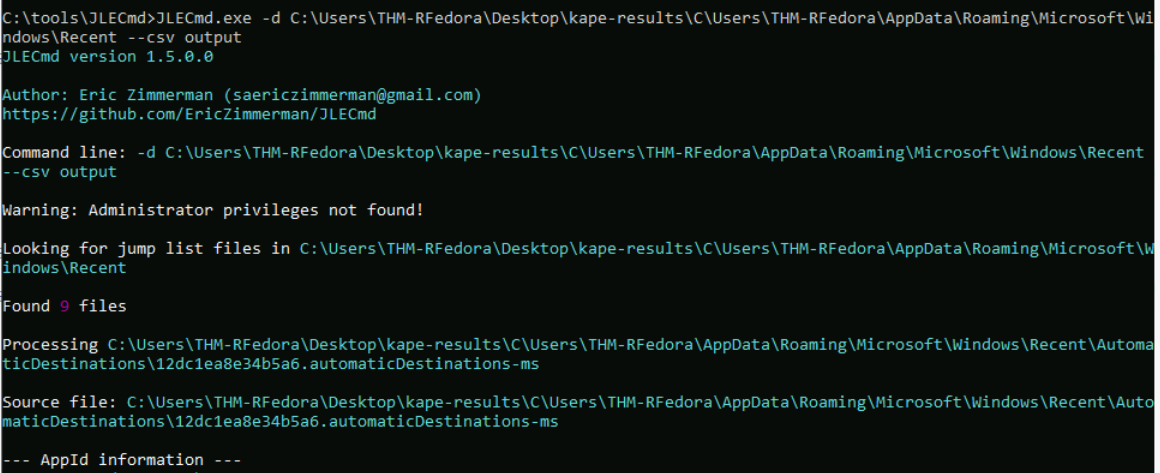
We can proceed with JLECmd.exe -d C:\Users\THM-RFedora\Desktop\kape-results\C\Users\THM-RFedora\AppData\Roaming\Microsoft\Windows\Recent --csv output command to parse all files inside JumpLists folder.
Now we should have 2 output files from AutomaticDestinations and CustomDestinations.
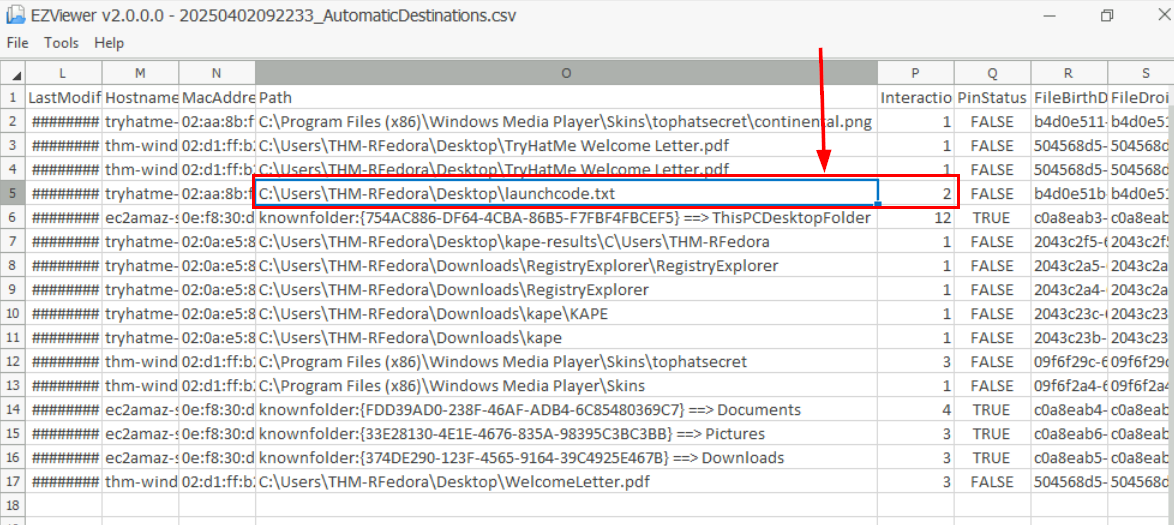
We don't have Timeline Explorer but we still have EZViewer so we could open AutomaticDestinations output file with it which we will see that the text file was opened 2 times from the interaction column.
2
When was the text file from the previous question last modified? (MM/DD/YYYY HH:MM)
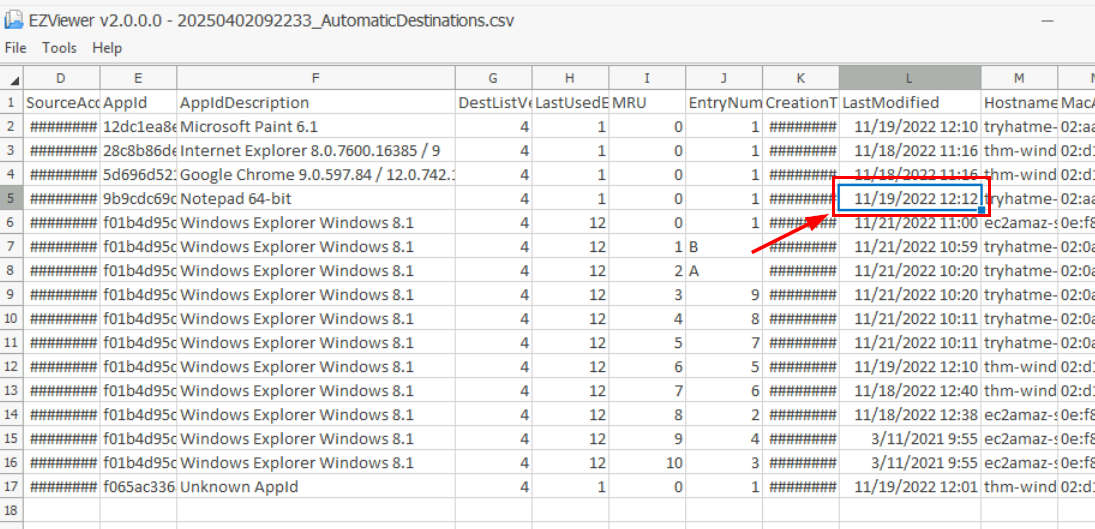
We have to get the value from LastModified column which we can see that the interaction timeline was align with the incident.
11/19/2022 12:12
The contents of the file were exfiltrated to pastebin.com. What is the generated URL of the exfiltrated data?
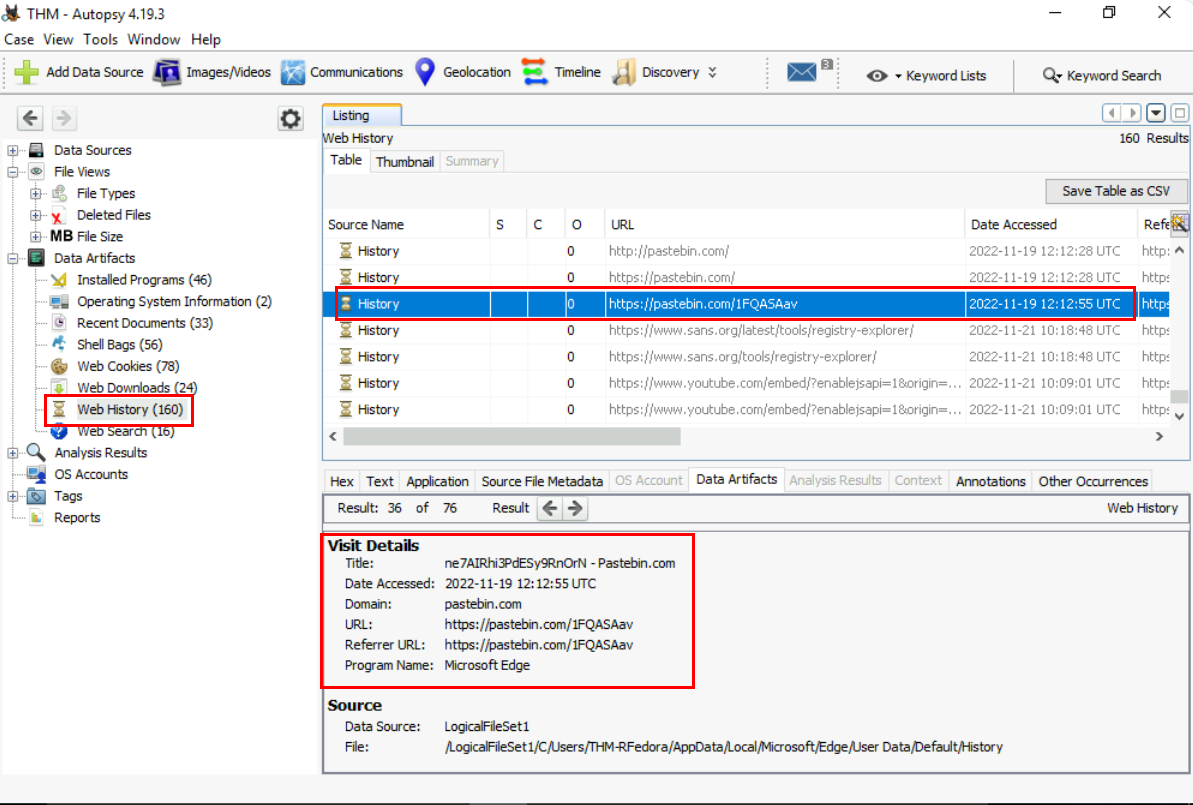
We will have to go back to Autopsy again to check "Web History" which we will see the pastebin URL that was accessed by user and the timeline also align within the incident timeframe as well.
https://pastebin.com/1FQASAav
What is the string that was copied to the pastebin URL?
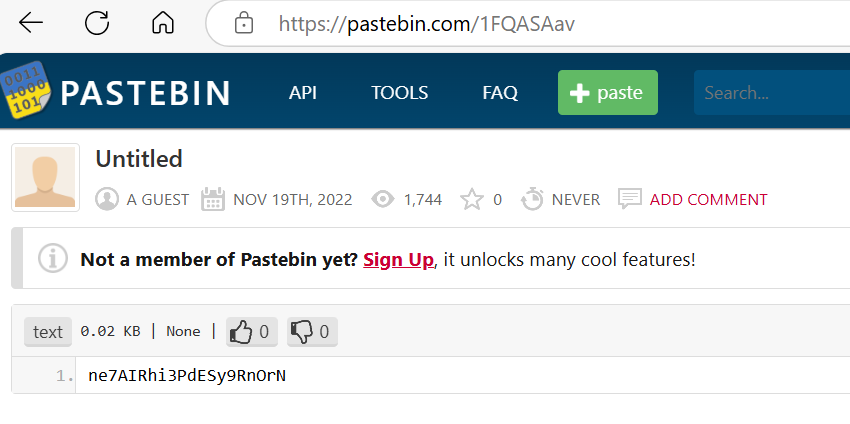
We can access this URL directly with our browser to get the content inside this URL.
ne7AIRhi3PdESy9RnOrN
And now we are done!